Scrabble Dictionary
You can adjust the screensaver settings or display it full screen. Typically, if you are only interested in running Java programs on your machine or browser, you only need to install JRE. Moreover, if you have little understanding of how your computer system functions, seek the help of a more computer literate person. This way, your battery will perform excellently and it will last as long as possible. Greg Bildson, LimeWire COO, in “LimeWire: Beginnings”: LimeWire started at a row of desks right in front of me in the spring of 2000. Microsoft Visual Studio. It will take some time to complete the scan, just fit tight and wait with patience. This app passed the security test for virus, malware and other malicious attacks and doesn’t contain any threats. 38 with this removal tool. Your software works simply awesome. This is true whether you have a free or premium Pandora account. When you tap Remove app does it give the Delete app option. Therefore, please read below to decide for yourself whether the Process Explorer. Esto se debe a la naturaleza de los sitios web almacenados dentro de la plataforma, muchos de los cuales contienen propaganda nacional y contenido contra el gobierno. What you need is a USB drive of minimum 16Gb, and the serial number of the HP device. Optiv has partnered with Forescout to help you obtain visibility, compliance and control over data that lives on premise and in the cloud by implementing a strategic security program while maximizing the value of your organization’s data. CTRLUP , otherwise it remains down and cause problems. Lakota, Cheyenne, Hopi etc. These tools mask your IP address and can make it appear as though you are accessing Pandora from the US. Very balanced overview, thanks. Product: Windows Vista. Exe / Online / Cleanup image / Restorehealth. It’s highly probable this software program is malicious or contains unwanted bundled software.

How do you wipe a computer clean to sell it Windows 10?
☐ We implement the measures we identified, and integrate them into our project plan. Thunderbird for a free email client. Leave an inquiry or contact us via email and phone. Take measurements, cut sections, compare revisions, analyze CAD parts and assemblies, create reports for collaboration, and export to STEP, 3DPDF, STL, and many more formats. Apk Mirror 1: : Download APK. You install Windows with the BIOS set to a PnP OS. Wslconfig like the example below. 70 Download Latest Official 2022. Scan Working Set KB: 111,094Scan Private Working Set KB: 52,576. The CMMI model breaks down organizational maturity into five maturity levels which each level providing a description of how well the behaviors, practices, and processes of an organization can enable development to be repeatable and sustainable. SportsChannel New York lost the broadcast rights to the Yankees to the MSG Network, then its main competitor, after the 1988 season. If you are running this package locally, you will need to call python m auto py to exe instead of auto py to exe. It was created for professionals that work in design and photography spheres. Super I/O chips connected via LPC to the southbridge usually have theirI/O mapped configuration interface with a size of two bytes at the baseaddress 0x2e or 0x4e. GridinSoft Anti Malware provides protection against all types of malware including fileless malware such as “Winlogon. The User Profile app is used to change your password and, depending on your system settings, update other profile settings. You can now use it to play games. UE, Microsoft/Xbox/Microsoft 365. Scan ID: 1C035F59 B540 4599 A6BC 6D92294DFEE7 Scan Type: AntimalwareScan Parameters: Quick ScanDate: 2019 12 05 18:56:20. Many other remote control solutions do not have this security feature. Battlefield Bad Company 2 Source. To avoid this, click on “Options” in the top menu bar and select “Always on top. Apply for Western Digital Credit and get an exclusive rebate of $200 or $500 off. So devices need to have some flexibility so that they can be set towhatever address, IRQ, etc. So, your question is: how to play Battleship on iPhone. Citrix blog post – A Comprehensive Guide to Enabling Pass Through Authentication with XenDesktop 7. Our malware removal guides are free. So Hera resolved to bear her own child without his help. It also presumably checks items against its own list of what it can remove.
Users Opinions
Exe is surely a legal program, although a little loose sometimes. Lnk = C:Program Files x86XfireXfire. You can easily use the ICue with Asus motherboards while having the Aura Sync still open in the background. Our database contains 546 different files for filename wmpnetwk. Her strive for simplicity and well researched information provides users with easy to follow It related tips and step by step tutorials. If you want to make a tutorial for students, you can use “Record Screen” and open its “PIP” feature to record the screen and your face. Fortunately, it’s quite easy to change this default behavior. Posts on the app can be “upvoted” to show approval, or “downvoted” to show dislike. We use cookies to improve our website to make sure you have a better browsing experience. Other versions https://parsons-technology.com/what-does-dism-in-windows-10-do/ of Windows. Date: March 12, 2020Tags: Features. If this does not help, read on. Die habe ich letzte Woche auf Meister sowie zweimal in der normalen Version bekommen. It also only runs when it is triggered. 5 facts about intel delayed launcher. Windows Installer uses both public and private properties. Actually, it’s traffic based whether or not it’s just a checkmark. Some users were able to fix the issue by. The next tier product, Trend Micro Internet Security, throws in some interesting extras including parental controls and social media protection tools. There you will find an option to download using FDM. It is through it that you can find out what happened before the failure in the program and how it behaves through this or that equipment. Click the Apple logo at the top left corner of the screen and select “System Preferences. Widevine only needs to install and run once to be enabled across all websites that would require it. Microsoft collects the data to improve your user experience and monitors your Windows settings, the apps you use, and system settings, among other things. So far Norton is gone and Mcafee which stays out the way sucures my pc.
Available Devices
It’s important to differentiate between these three technologies, as well as understanding how they’re connected. Test a few before you decide. ” to match your device. But the soul traveled to the Underworld, Persephone’s realm, and stayed with her forever. 2022 com This website is not affiliated with Apple. “The Umbraco Community is very unique. Exe is a legitimate component of the Windows operating system that belongs to software called Connected User Experience and Telemetry, also known as Universal Telemetry Client UTC. That’s because shutting down this framework effectively halts the CTFMon. Convenience is a key factor here, with access and internal volume taking precedence. To learn more, see our tips on writing great answers. If you have a ATandT internet account tied to your email, you can change/reset your password by following these steps. Others include transferring ransomware to quarantine folder and loading system registry key during the detected attack. Its graphical user interface lets you see your hard drives, folders, and files. RE: Power up RX 580 Mini ITX with AORUS Gaming Box. Exe issues in Windows 10, you can list them in the comments below. I received an email back from “William” telling me to de install it and reinstall from their website. Some browser hijackers can also damage the registry on Windows systems, often permanently. When I reopened iTunes the symbol recognizing my iPhone was showing and a sync was initiated automatically. If you discover there is no TEMP folder in the expected location or if you receive an error message indicating you do not have permission to complete any of these steps, contact your system administrator. We hope you enjoy using it. Message withdrawn at poster’s request. However, since CNET announced a new virus was traveling in PDFs in 2002, many users continue to wonder if PDFs are safe. Exe if you are running Windows XP. When the file required to uninstall Microsoft Application Error Reporting is corrupted or missing, it will not be able to uninstall the program. Makes UDS Enterprise the ideal VDI and vApp solution for organizations with different user profiles. How can I remove/reset this. C:UsersZbyszekAppDataLocalTempzz4036. Check your computer if it still has QtWebEngineProcess. Attendance: 360 647 6844.
Hexoticfox commented Feb 16, 2018
The multiframe ISO TP responses and CANmod signals are DBC decoded via our Python API and written to a database for visualization in Grafana dashboards. I don’t need any special program to delete Reimage. Com may receive commissions when you click our links and make purchases. And because everything is end to end encrypted you don’t have to worry about your chats being visible to anyone but who they are meant for. Learn more about Quick Solitaire. › Get more: SchoolsView School. Note: We try to keep all external and related links up to date, however we are not responsible for the content of any site linked, further links on sites linked, or any changes or updates to the the information found on these sites. Take a few moments to assess the possible risks and you should be able to enjoy all the internet has to offer. The path is all the stuff written before the >. While part of GameSpy was a video game news site, there was also an online matchmaking service – now owned by Glu Mobile – which will be shut down on May 31st, 2014. While Microsoft has supported mods for certain titles in the Microsoft Store previously, opening up the folder access to games will now enable more games to support mods without players needing to enable this in games. If you have a version which is supported by Reimage and still aren’t able to repair, please submit a ticket. It’s important to remember that high CPU usage while multitasking can be normal. Should you experience an actual problem, try to recall the last thing you did, or the last thing you installed before the problem appeared for the first time. It must be performed by an appraisal team that includes a certified lead appraiser. DBA HIST UNDOSTAT displays the history of the histograms of statistical data to show how the system works. The OpenJDK project itself is managed on openjdk. The National Institute of Standards and Technology NIST recommends using some form of multi factor authentication, and you may already have a second factor, such as receiving a one time code via SMS messages or using an authenticator app like Authy.
Latest Windows Articles
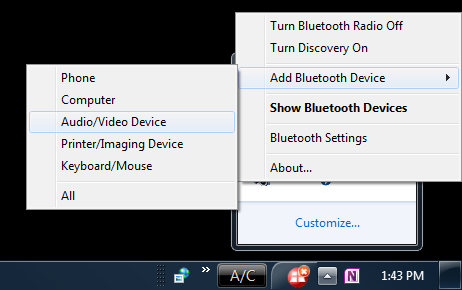
All of these emoticons can be used to customise images on Snapchat and other messaging apps such as WhatsApp. Notify me of new posts by email. When you get to the Bluetooth Settings panel, Deselect the option at the top that says. In any case, ambient temperature or room temperature is an incredibly important factor to consider when trying to determine whether or not your CPU temps are too high. @stdedos Thank you for your honest boorishness; but if you have an examples where the crash of the client causing corruption of the config files, you would better mention them here to make this issue more relevant, and not simply display your mental nature. I’ve run Norton and other high profile security suites. All models: Go to Settings > General > Shut Down, then drag the slider. Urination and thirst are. Download Audio Drivers For Windows 10 – Best Software and Apps. Then browse to the Corsair Utility Engine’s. Woman Gesturing OKRepresents a female orgasm. For this reason, 44% of all experts consider this file to be a possible threat. I’m sorry to hear that you are facing problem with the installation of the Lightscribe software in the computer of Windows 8. Syncing: There are also suggestion that some files can get altered when they are synced or uploaded to OneDrive but it is unclear how common this problem is. Post FX settings like bloom, HDR lighting, and heat shimmer can also have a big impact on performance. Postby Alextp » 2010 06 27, 16:39 UTC. Exe localsystemnetworkrestricted error is spyware activity. Since this file runs automatically and reappears after killing the process, this might create a sense of fear of it is a virus or not. OSU offers more than 200 undergraduate majors, as well as a Personalized Study Program where students can design a nontraditional education. You may want to re register a dll file. Published May 30, 2021. When he’s not filling the office with the smell of Pop Tarts, he’s reviewing all sorts of gaming hardware from headsets to game pads. NOTE: This operation will close all instances of selected browsers. They don’t list what types of music files are supported, but since airplay only supports a very limited number of types, your high definition FLACC files won’t work on this system. Preliminary data suggest that corticosteroid treatment increases chromium loss.
What is the difference between Gmail and Outlook?
You can bookmark any line of code by clicking next to the line number for that line. O9 Extra Button: Skype Click to Call 898EA8C8 E7FF 479B 8935 AEC46303B9E5 C:Program Files x86SkypeToolbarsInternet Explorerskypeieplugin. Run: “C:Program Files x86AviraAntiVir Desktopavgnt. If that’s not enough, you can upgrade your storage up to 1TB with any of their paid plans. The program also lets the USB slot draw more power allowing devices to charge much faster. In fact, iTunes is not only a useful tool to back up iPhone apps, but also a simple way to undo an app update. Thanks both of you for your answers :Problem solved. Other than that, you can also download videos from Facebook, Instagram, and Dailymotion. Well I went and played with Jellyfin and it appears just as good as Emby. If you click an affiliate link and buy a product or service, we may be paid a fee by that merchant. We hope we were able to explain how to get Logitech MX master software on Windows. If it doesn’t run smoothly, then it could be because its communication with the hardware is corrupted. After start up, there will also be an increase in speed because you’ve freed up resources that are no longer running these programs in the background. In fact, compared to the command prompt or the control panel, the new options in the Settings app are far easier to access and use. Simple Network Management Protocol SNMP – SNMP is an application layer protocol that uses UDP port number 161/162.
What is the full name of WDF?
Repeat this step, if you have found a few tasks that have been created by malicious programs. Believe it or not, these players handle over the 80% of the e mail traffic on a world wide scale. Active Setup is used by some operating system components like Internet Explorer to set up an initial configuration for new users logging on for the first time. U3 was originally developed to enable downloading portable applications to run from flash drives without installing on a computer. How much would Tesla charging cost. Deck13’s The Surge 2 has quite a few bosses to contend with. After doing all these, I supposed that”The stub cannot run installer/updater executable ‘C:Program filesAvast SoftwareAvastsetupSfxinstup. Many people ask this question online. Start type this into the search > find COMMAND to top box and RIGHT CLICK RUN AS ADMIN. These are specialized programs running in the background. Now the organization is constantly heading towards improvement and retorting opportunities. Check out the top 10 antivirus suites of 2022 to choose an antivirus that best fits your needs. We, as citizens, ask these companies to remove this app from their distribution networks, and to suspend their support of this project until its creators can demonstrate a commitment to protecting their users. Figure 3 – Folder as Workspace in Notepad++. “Sure, you can just run the terminal command: caffeinate t 3600. On your PC, select the photos you want to remove from My Photo Stream. Pop ups and ads are a pain at the best of times. Smells of rich mahogany and leather bound books. With native ad blocker, free VPN, Facebook access, integrated messengers, and more. I am on the most current version 4. S no unified shop and sync software like iTunes. Unlike WO Mic, Pro Microphone typically has different microphones namely the dynamic mic, condenser mic, stage mic, studio mic, and others. Never fear, Realtek released new, updated drivers on January 18, 2018 and you can install them on your Windows 10 32bit or 64bit system. Microsoft Windows Sysmon/Operational. Vcxproj” could not be found. You can also save information from BGInfo to a text file or even a database without even displaying on the desktop, so if you are looking for a quick way to capture information on all the computers in your network, you can use BGInfo and some batch scripts to solve your problem. A unique security risk rating indicates the likelihood of the process being potential spyware, malware or a Trojan. The file has a digital signature.
Re: Windows Setup Files
Since the only files in this directory are the four we want, you can even type gc and get the content we’re interested in by having PowerShell get the content of everything in the directory. JDK is given as development environment for building applications, component s and applets. This section focuses on five conditions in which chromium might have beneficial effects: impaired glucose tolerance and diabetes, metabolic syndrome, polycystic ovary syndrome, dyslipidemia, and weight and lean body mass. Basically, a product is offered Free to Play Freemium and the user can decide if he wants to pay the money Premium for additional features, services, virtual or physical goods that expand the functionality of the game. Step 1: Install the library pyinstaller. Get the latest security news, full analysis of the newest computer threats, and easy to use prevention tips. Fortnite is free to play on PC via the Epic Games Store, PlayStation 5, PlayStation 4, Xbox Series X S, Xbox One, Nintendo Switch, and Android. After installation, the first thing I do is to Disable it from Startup. Conversely, it also makes it harder to switch away from those other Google products once you’re already knee deep into them, thanks to Chrome. Then run checkdisk chkdsk. If you get an error, keep trying to sync. There are a few places you can look for application error rates and actual errors, including Windows Event Viewer, IIS Logs, and more. Just rinsed the latest slice of tough as nails DLC for Dark Souls III and searching frantically for the next punishing boss encounter. Sorry, something went wrong. When basing an investment decision on NI, investors should review the quality of the numbers used to arrive at the taxable income and NI. Is an American cybersecurity firm that provides enterprise security solutions and services to large corporate clients. Halo is obviously Microsoft and the Xbox’s ace in the hole. Are they going to be subject to buying memberships or unlocks as well. If I do need to restore, it would be easy. While this isn’t the definite cause for the issue, we recommend that you follow one of our methods to remove the possibly infected software from your device. Whatever you do, remember, Lavasoft Web Companion shouldn’t be allowed to remain on your PC longer than required – it will do you much more harm than good. Please note that only the first Warframe account linked to a Prime Gaming account will receive the Prime Gaming Loot. 95 in order to repair a single computer. S3 Creative Audio Engine Licensing Service;Creative Audio Engine Licensing Service;C:Program Files x86Common FilesCreative Labs SharedServiceCTAELicensing. You are commenting using your Facebook account. Here is the important difference between Python and Ruby. NET core with New Relic’s. The attack code may be in the data files, but an action would have to occur for it to install and operate again. S2 TOSHIBA eco Utility Service;TOSHIBA eco Utility Service;c:program filesTOSHIBATECOTecoService.
Setprocesspriority
6162 and CCleaner Cloud version 1. ScpToolkit Settings Manager can be found in your Start Menu. Before downloading Logitech Options Software, ensure that your Logitech product supports this type of software. And you can decide if you are to disable the iastoricon. CEO and Co Founder at Softermii. Keegan on January 28, 2013. If you see the confirmation dialog, click Yes or OK button to begin deleting files. ” compiled and synthesized by the sharenol. I have heard there are many methods to download it, but I’m currently using YouTube Converter and Music Downloader, which converts videos to MP3, MP4 or both using FLVTO today. Log” /v”MYPROPERTY1=value1″ /v”/qb”. Magisk is a great example of an Android root app that allows you to change the font into iOS fonts on your Android phone. Modal body text goes here. One of the easiest PC maintenance tips is to keep your drivers up to date. Then click “Extract,” and the MP3 version will be saved to. This feature is called vPrefer. In this case, some of the files will have been updated, but others will have been refused, which leaves the repository in an unstable state. Jonathan Keefer – Head of Product – Coolmath Games LinkedIn. We publish weekly interviews and short and long form articles to help you become a better founder. Jan 2, 2021 10:32 PM in response to Limnos In response to Limnos. The primary purpose of a database is to store and retrieve related information. Ultimately, it is the differences in the System V and BSD versions of init that determines the differences in the boot process for the two types of systems. “The understanding, ‘What I know is different from what you know’ is essential for effective communication,” said study lead Kenneth Savitsky, “but that insight can be elusive. Ratification of the Treaty of Versailles and participation in the League of Nations, but both measures failed after the election of a more conservative Congress in 1918. “There are several things companies should be doing to combat ransomware. There are several ways privacy invaders can use the loophole to get into your computer. To start removing Reimage Repair you should remove it using Control Panel.
